The FBI has issued a warning that BADBOX 2.0 malware is surging through residential consumer electronics, infecting millions of internet-connected devices. The malware, often preloaded onto inexpensive streaming hardware and IoT devices, can steal your data and provide backdoor access to the device—and is extremely difficult to remove.
The BADBOX 2.0 Botnet Is Back
BADBOX 2.0 is the evolution of the original BADBOX malware. This malware was first identified in 2023, though it was partially taken down by a German cybersecurity agency that sinkholed the communication between infected devices. It disrupted the malware, but didn’t completely eliminate it.
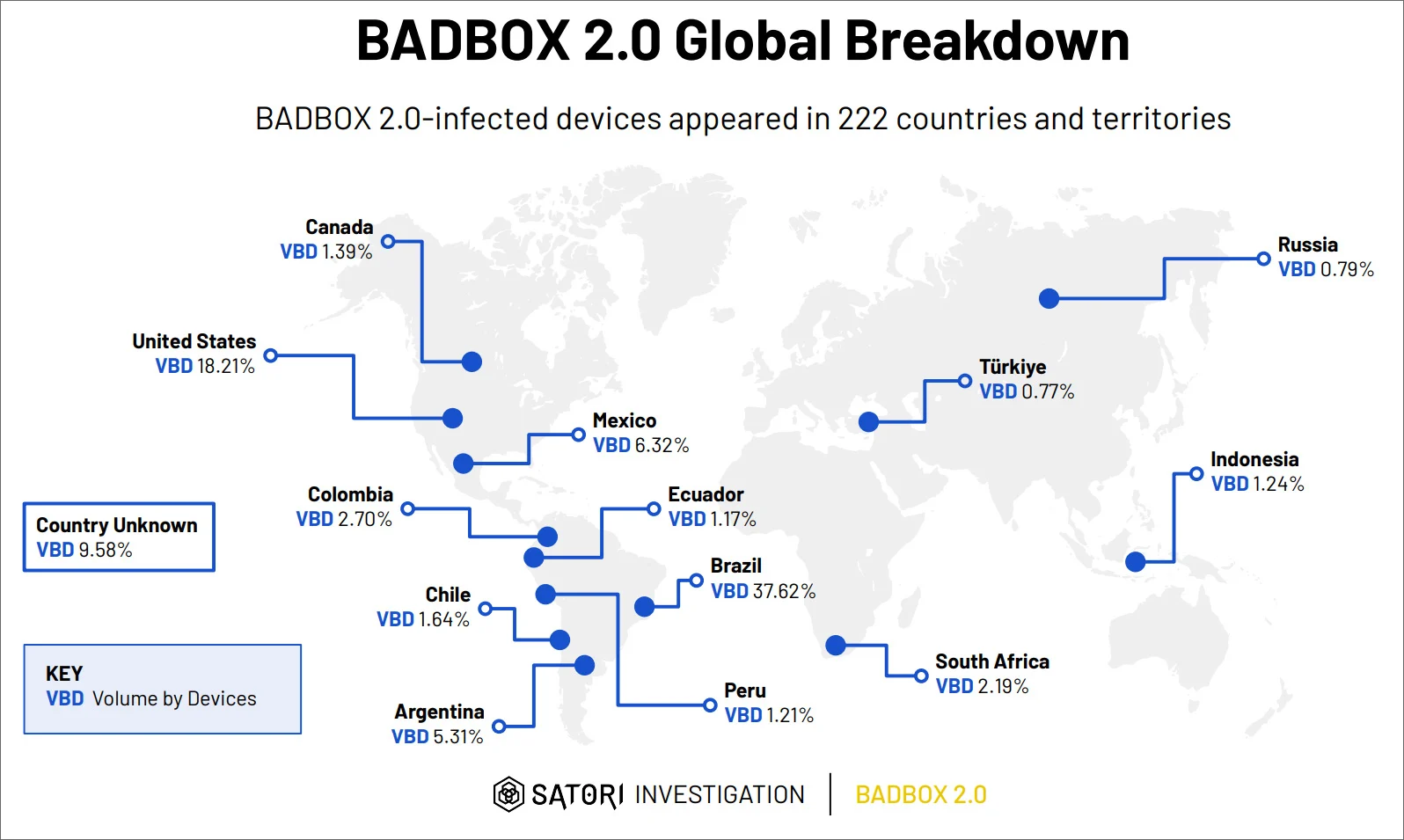
Now, BADBOX 2.0 has built a massive botnet comprising more than one million devices, including smart TVs, IoT devices, streaming boxes, projectors, tablets, and more.
The FBI’s BADBOX 2.0 public service announcement revealed that most devices are preinfected with malware at the point of sale, with most coming from China.
Cyber criminals gain unauthorized access to home networks by either configuring the product with malicious software prior to the users purchase or infecting the device as it downloads required applications that contain backdoors, usually during the set-up process.
Once you connect an infected device to your network, it can “phone home” to the control network, which can in turn activate the BADBOX 2.0 malware. Once activated, your device becomes part of the BADBOX 2.0 botnet, and there may be little indication that you have an infected device in your home.
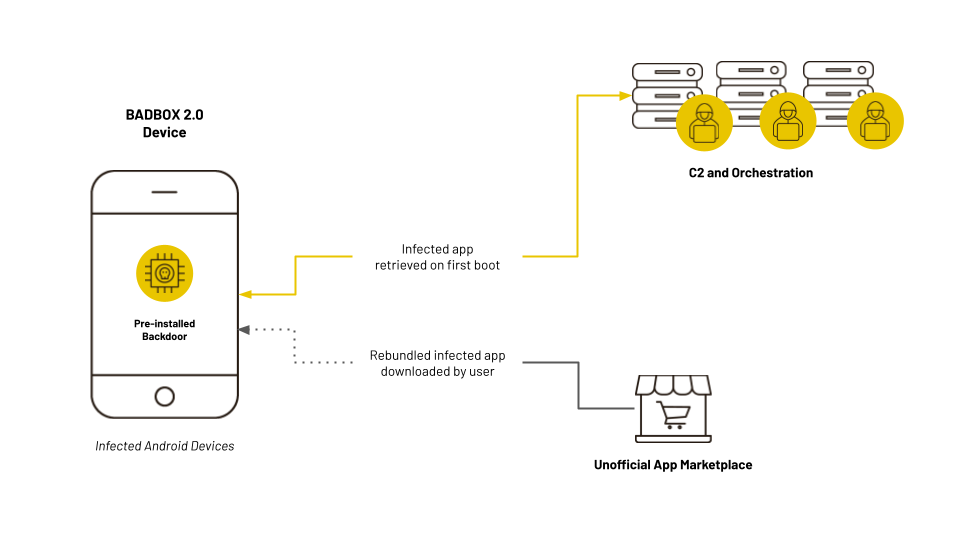
However, it’s not just preinstalled devices that contain BADBOX 2.0 malware. Where BADBOX relied primarily on this method, BADBOX 2.0 has been spotted using drive-by downloads to infect other devices. Similarly, the malware has been bundled into apps available for download on third-party Android marketplaces. This is why sideloading Android apps is such a danger.
What Does BADBOX 2.0 Do?
According to Human Security, the security research team that first revealed BADBOX 2.0, the evolved malware has a range of dangerous and sneaky attacks.
- Programmatic ad fraud
- Click fraud
-
Residential proxy services (basically selling access to your internet-connected device, which can then be used for additional attacks):
- Account takeover (ATO)
- Fake account creation
- DDoS
- Malware distribution
- One-time password (OTP) theft
What makes BADBOX 2.0 so concerning is that all of this activity takes place without alerting you. It’s not a type of malware that makes a song and dance about its presence; it wants to remain silent for as long as possible to maximize its chance of exploiting your device and data.
How to Check for BADBOX 2.0 Malware
First up, if you haven’t bought a Chinese streaming box or other Chinese internet-connected tech, you’re probably in the clear. However, check if you own any of the infected devices, as per Human Security’s table:
Device Model | Device Model | Device Model | Device Model |
TV98 | X96Q_Max_P | Q96L2 | X96Q2 |
X96mini | S168 | ums512_1h10_Natv | X96_S400 |
X96mini_RP | TX3mini | HY-001 | MX10PRO |
X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
X96QPRO-TM | sp7731e_1h10_native | M8SPROW | TV008 |
X96Mini_5G | Q96MAX | Orbsmart_TR43 | Z6 |
TVBOX | Smart | KM9PRO | A15 |
Transpeed | KM7 | iSinbox | I96 |
SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
X96Q | isinbox | Mbox | R11 |
GameBox | KM6 | X96Max_Plus2 | TV007 |
Q9 Stick | SP7731E | H6 | X88 |
X98K | TXCZ |
Next up, conduct a review of all of your internet-connected devices, no matter their origin. Check for suspicious app marketplaces that you haven’t installed, altered settings, and other changes to your devices you don’t remember making.
Unfortunately, removing BADBOX 2.0 from most devices is a difficult process because it involves flashing a new, clean firmware. For many cheap streaming boxes and IoT devices, a separate firmware update may not be available, which means you’ll have to cut your losses and ditch the device to protect your network and data.








